In this article, I will show you Windows BitLocker configuration using Intune. BitLocker encrypts the hard disk data to prevent data loss if a device is stolen/ lost.
If the device is stolen or lost, data is secured. Others can still format the system but won’t be able to get the data. 265-bit encryption has a 48-digit recovery key which can’t be easily recovered with a password generator tool, it will take ages to crack the recovery password.
We can set up a rotation of the recovery key, this will refresh the BitLocker policy on the period. Recovery Password Rotation is a setting which is part of BitLocker policy. This allows to recreate of the recovery password once the recovery password is utilized.
Pre-requisites of BitLocker
- TPM (Trusted Platform Module) chip version 1.2 or 2.0
Intune configuration
Let’s configure BitLocker encryption in Intune. There is multiple ways to configure but I will take you through Endpoint security options:
- Go to Microsoft Intune admin center
- Navigate to Endpoint Security
- Go to the Disk encryption” section and Create a new policy
- From Create a profile, select the platform as Windows 10 and later choose profile as BitLocker and click Create.
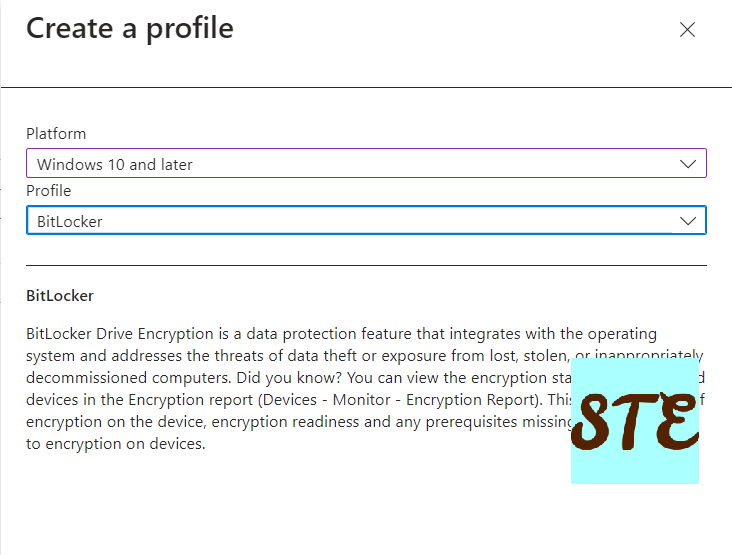
- Provide the name and description as you required
- In the next stage, Configuration settings set value for BitLocker and Administrative Templates
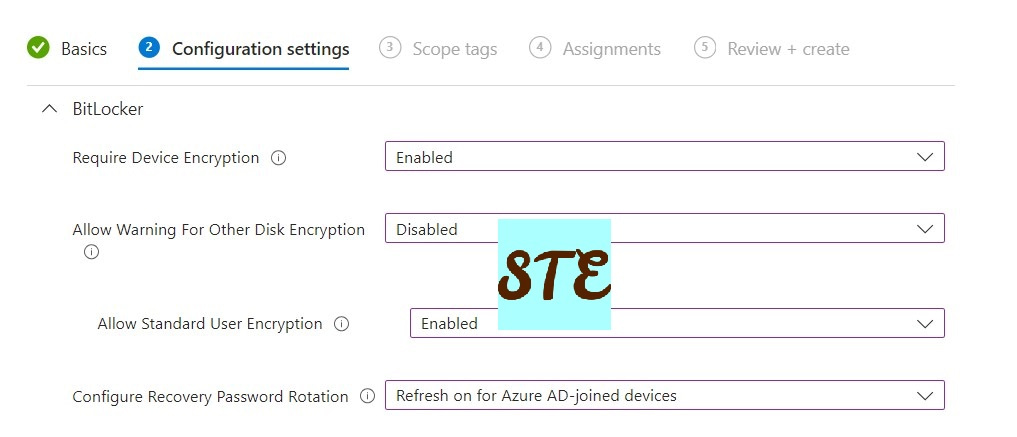
- Under BitLocker, specify the following:
- Require Device Encryption = Enabled
- Allow Warning for Other Disk Encryption = Disabled
- Allow Standard User Encryption = Enabled.
- Configure Recovery Password Rotation =Refresh on for Azure AD-joined devices. You can choose the Hybrid option as well if your organization is still in Hybrid mode.
- Under BitLocker, specify the following:
-
- Expand the Administrative Templates section:
- BitLocker Drive Encryption
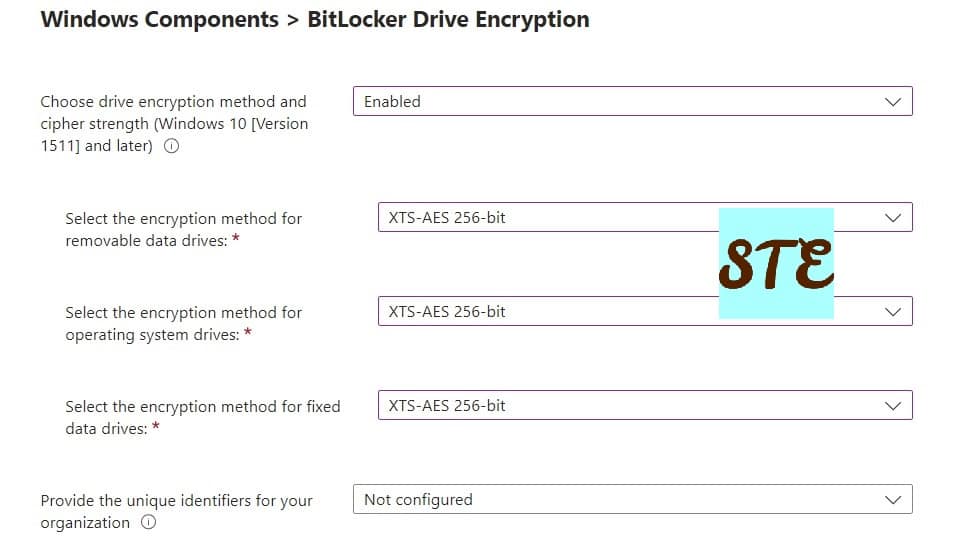
- Choose the drive encryption method and cypher strength = Enabled.
- Select the encryption method = XTS-AES 265-bit
- BitLocker Drive Encryption
- Expand the Administrative Templates section:
-
-
- Operating system drive
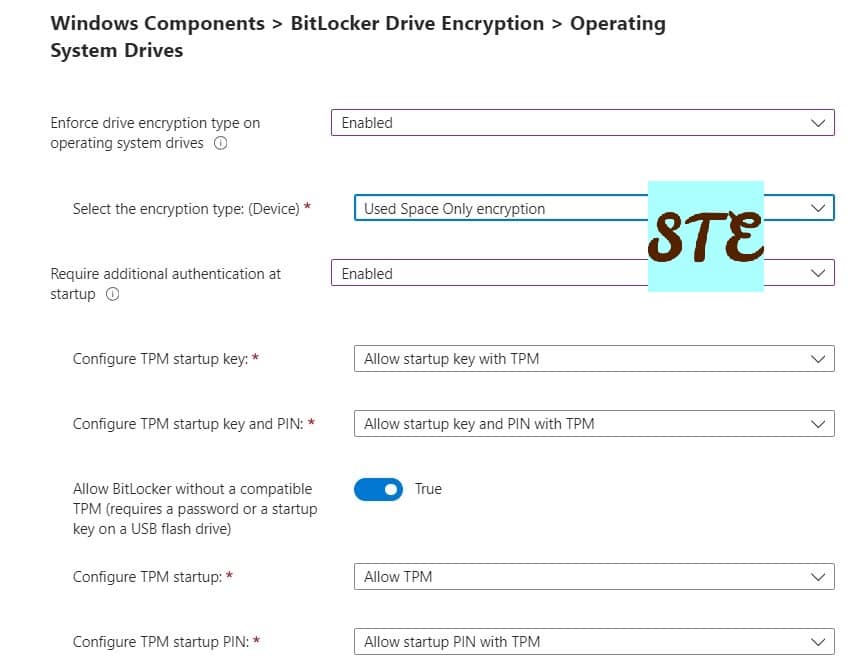
- Enforce drive encryption type on operating system drives = Enabled.
- Select the encryption type: (Device) = Used Space Only encryption.
- Require additional authentication at startup = Enabled.
- Configure TPM startup key and PIN= Allow startup key and PIN with TPM
- Configure TPM startup = Allow TPM
- Allow BitLocker without a compatible TPM = True
- Configure TPM startup PIN = Allow startup PIN with TPM
- Configure TPM startup key = Allow startup key with TPM
- Operating system drive
-
-
-
- Fixed Data Drives
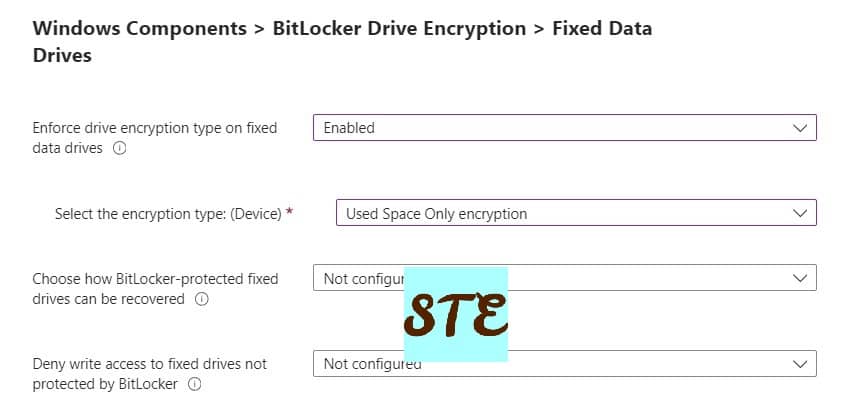
- Enforce drive encryption type on fixed data drives = Enabled
- Select the encryption type: (Device) = Used Space Only encryption
- Fixed Data Drives
-
-
-
- If you require, you can configure Removable data drives.
- Set the scope tag or leave it for default
- Select the appropriate assignment and save the configuration policy.
-
Verify BitLocker Encryption status
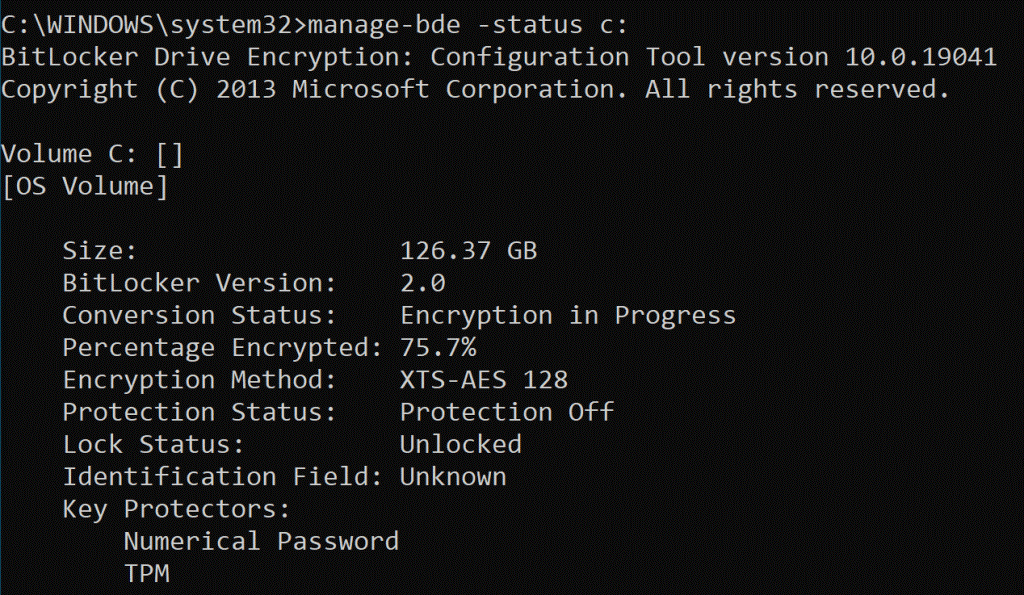
Check the status in Intune if the policy is applied on all intended systems, you can check on the system.
- Open the command prompt as administrator and run the command: Manage-bde -status c:
To find the recovery key of the device,
- Go to Microsoft Intune admin center
- In Devices Search for the device.
- In Device, click on Recovery keys.
- We can see the BitLocker Key and click on Show Recovery Key, it will present 48 keys.
That’s it.
Check out more about Intune & I have a specific section for Windows troubleshooting I hope you will like to explore.